Sam360 supports portal authentication using Microsoft Entra single sign-on. It is Sam360’s recommended authentication mechanism. It has the following advantages over Sam360 standard user authentication.
- Streamlined User Experience
- Simplified Login Process: Users can access Sam360 along with other corporate resources using a single set of credentials. This eliminates the need to remember and manage multiple usernames and passwords, reducing login fatigue and streamlining access.
- Consistent User Interface: Entra SSO can provide a consistent login experience across all applications, aligning with the rest of an organization’s ecosystem.
- Enhanced Security
- Centralized Authentication: Entra SSO centralizes the point of authentication via Microsoft Entra ID, which reduces the potential attack surface by limiting the number of systems where user credentials are stored and managed.
- Robust Authentication Options: Entra ID supports advanced authentication mechanisms, including Multi-Factor Authentication (MFA), which significantly enhances security by requiring additional verification of user identities.
- Conditional Access Policies: These policies allow organizations to apply specific conditions under which users can or cannot access certain applications. For example, you can restrict access to applications based on the user’s location, device compliance status, or risk level.
- Reduced IT Overhead
- Easier User Management: User access can be managed from a central location. Adding or revoking access to Sam360 can be done easily through Entra ID without having to manage separate user databases.
- Automated Provisioning and Deprovisioning: Integration with Entra ID can allow for automatic user account provisioning and deprovisioning as employees join, move within, or leave the organization, which helps in keeping user access current and secure.
- Single Point for Audits and Reports: Entra ID offers comprehensive logging and reporting features that simplify compliance reporting and audit processes. It provides detailed access and authentication logs that are crucial for security audits and compliance.
- Improved Compliance
- Regulatory Compliance: Leveraging Entra SSO can help in meeting various compliance requirements that mandate the use of strong authentication and detailed access logging.
- Data Privacy and Security: With Entra ID, sensitive user authentication data is handled by a platform that is continuously updated to comply with the latest security standards and regulations.
Enable Microsoft Entra SSO
Microsoft Entra SSO needs to be enabled in the Sam360 portal and the Microsoft Azure Entra ID portal. A user requires the ‘Tenant Administrator’ role in the Sam360 portal in order to enable SSO there. Depending on how an organisation has configured their Entra ID environment, it’s possible that all users are automatically permitted to use their Entra ID to authenticate to 3rd party applications including Sam360. If this is not the case, an Azure Administrator with one of the following roles is required to enable SSO with Sam360 there – ‘Global Administrator’, ‘Application Administrator’ or ‘Cloud Application Administrator’
Whilst Entra ID can be used to authenticate users, user roles still need to be assigned in the Sam360 portal. Sam360 portal users’ usernames should match their Entra ID User Principal Name (UPN)
- Log in to the Sam360 portal using standard Sam360 authentication. The user should have the ‘Tenant Administrator’ role in the Sam360 portal
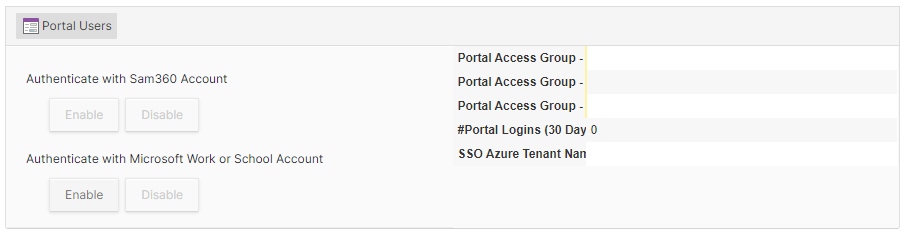
- Click on Settings->Portal Users. Under ‘Authenticate with Microsoft Work or School Account’, click ‘Enable’
- You may be asked to login with your Entra ID or choose an Entra ID if you are currently logged in with more than one identity.
- Depending on how Microsoft Entra ID is configured in your organisation, you should see one of the following options…
- You are a non Azure Admin and you are permitted to consent to 3rd party application SSO permission requests.
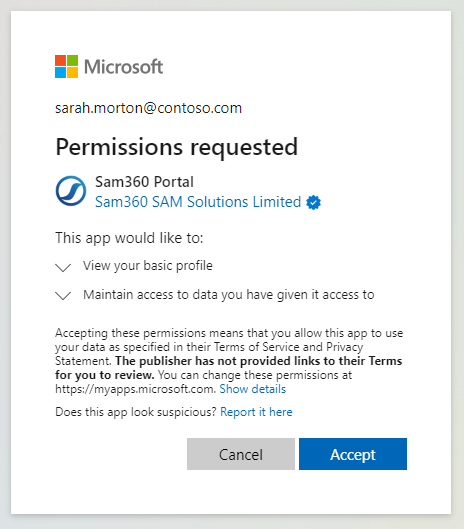 Click Accept. You are now logged in using SSO. You will not be asked to grant permissions the next time you sign in.
Click Accept. You are now logged in using SSO. You will not be asked to grant permissions the next time you sign in. - You are a non Azure Admin and you are required to request consent to 3rd party application SSO permission requests.
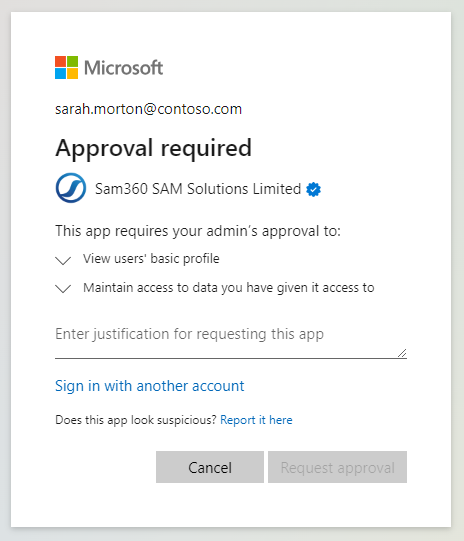 Provide an explanation of why you need access to Sam360. Your request will be forwarded to an Administrator within your organisation. If your request is approved, you should receive a notification by email. At that point you should be able to sign in to the port using your Entra ID.
Provide an explanation of why you need access to Sam360. Your request will be forwarded to an Administrator within your organisation. If your request is approved, you should receive a notification by email. At that point you should be able to sign in to the port using your Entra ID. - You are a non Azure Admin and users are not permitted to access or directly request access to use SSO with 3rd party applications.
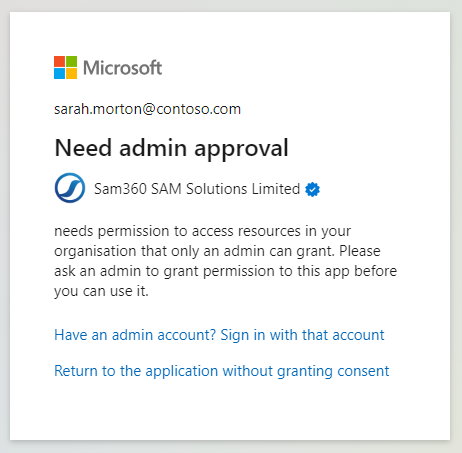 You will need to request approval for SSO to the Sam360 portal using your standard support channel.
You will need to request approval for SSO to the Sam360 portal using your standard support channel. - You are an Azure Administrator.
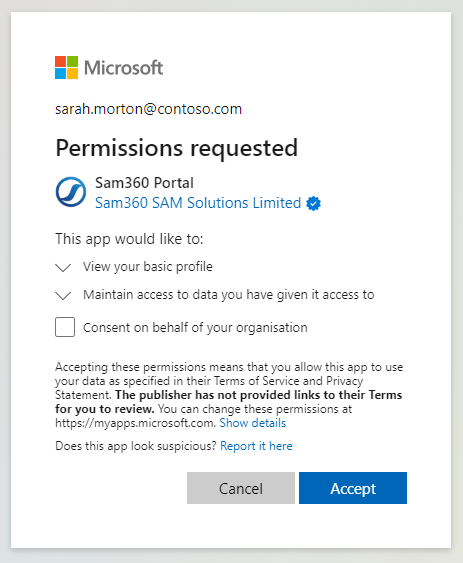 Click ‘Consent on behalf of your organisation’ and ‘Accept.’ Whilst all users can now authenticate to Sam360, only users that have been granted permission to access the portal will actually be able to sign in.
Click ‘Consent on behalf of your organisation’ and ‘Accept.’ Whilst all users can now authenticate to Sam360, only users that have been granted permission to access the portal will actually be able to sign in.
- You are a non Azure Admin and you are permitted to consent to 3rd party application SSO permission requests.
- Once Entra SSO is enabled, it is possible to disable standard Sam360 authentication. Click on Settings->Portal Users. Under ‘Authenticate with Sam360 Account’, click ‘Disable’
Once the ‘Sam360 Portal’ application has been authorised for use by one or more users, it will appear in the Azure portal in the ‘Enterprise Applications’ blade. From there it can be further configured to add/remove access for user and groups and apply ‘Conditional Access Policies’ etc.




Leave A Comment